Gaming companies process billions in transactions annually, while safeguarding vast databases of customer financial information, making them prime targets for cybercriminals seeking both immediate payback and valuable data. During the panel “From Recon to Compromise: Defending Against Modern Threats in the Gaming Sector” at this week’s Canadian Gaming Summit, Microsoft Global Black Belt Nick Selvaggio demonstrated how organizations of all kinds remain vulnerable to surprisingly simple attacks, demonstrating a live hack of a fictional Contoso Casino.
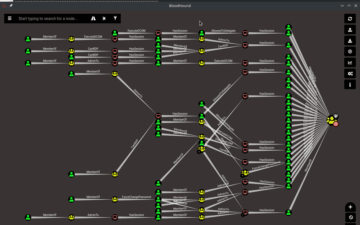
Selvaggio emphasized that an attacker’s first target is rarely the endgame, but rather a path to gather further information about an organization’s systems. He demonstrated this concept using Bloodhound, a tool hackers use to organize their path from low-security entry points like QA systems toward figuring out which employees have access to critical infrastructure and administrative controls.
QR code phishing, or “Qhishing,” involves the target scanning a QR code that looks official, but instead forwards the unsuspecting user to an attacker-controlled website. Qhishing is particularly effective, since the user is almost always on a mobile device. “And in the end, because it’s done on a mobile device, which typically has a very limited screen size, it’s harder to actually notice problems with the URL, that it may not be legitimate,” Selvaggio warned attendees.

Malicious QR codes can be delivered digitally or physically as flyers or stickers and they may not even target employees of your company, but suppliers that installed an HVAC control system or even a fish tank (in 2017, a casino’s high roller database was hacked through a smart thermostat in a newly installed fish tank).
“Defenders have to be perfect, but attackers just have to find one flaw,” Selvaggio explained.
The attack on Contoso Casino (note: Microsoft has been using the fictional Contoso Corporation in demos for 30+ years) began with gathering public technical information about the casino’s digital infrastructure using their public web URL (e.g. contosocasino.com). Public web URLs act as a relay, guiding different requests to different web servers.
Selvaggio’s probing revealed a few systems, including a quality-assurance (QA) portal for the company and an admin panel. “I probably wouldn’t go after [the admin panel] first,” he explained, demonstrating attackers’ preference for systems that may be an afterthought security-wise.
With the QA portal in sight, Selvaggio purchased the domain cont0socasino.com (did you spot the zero instead of an o?) and designed a login page that mimicked the real site.
The target employee on the other side of the conference room scanned the QR code from a bogus company bonus email (that showed hallmarks of a phishing email with its “URGENT” header). These differences are hard to detect on a mobile device’s small screen, especially when moving quickly to meet a deadline. The employee typed their username and password into the system, allowing Selvaggio his entry point into Contoso Casino’s systems.
The compromised QA portal transformed into an intelligence goldmine. The AI-powered chatbot freely shared the employee handbook, containing detailed security policies and procedures, along with the company’s cyber insurance-policy details, all useful information for a hacker designing further attacks to get into deeper systems and maximize payout.
So what can casinos and other organizations do to limit entry points?
The big takeaway from Selvaggio’s demonstration was this: Organizations must use multi-factor authentication. “And ensure that it’s on [all your systems]. If you use MFA, your risk reduction is 99.22%.”
For internal AI company chatbots, content-safety filters can detect and block prompt injection attempts before sensitive data exposure occurs. Selvaggio demonstrated that with a content-safety filter enabled in the AI chatbot’s backend, it refused to give sensitive information and sent a flag to Contoso Casino IT admins, who could then cut off the hacker’s access to the system.